Managing and provisioning resources efficiently is key to building successful applications in the cloud. AWS CloudFormation offers a powerful solution that allows developers to define and manage infrastructure using code.
However, ensuring security while leveraging CloudFormation's capabilities requires an understanding of its Service Role.
This guide will take you on a journey through CloudFormation, emphasizing the criticality of the Service Role. By following our step-by-step instructions and gaining practical insights, you will learn how to maximize the benefits of CloudFormation, streamline resource provisioning, and maintain a high level of security for your AWS resources.
The Fundamentals of Working With CloudFormation
The overall developer experience when working with CloudFormation involves:
Define your template: Use a CloudFormation JSON or YAML template to define the AWS resources you need to deploy and their configuration parameters.
Validate, test, and review: After creating the template, use the AWS CloudFormation console or AWS CLI to validate it for syntax errors. Test and review it to ensure it deploys the necessary infrastructure components.
Deploy your template to create a stack: When the template is ready, you can launch the CloudFormation template to create a stack. A stack is a collection of AWS resources you can manage as a single unit with the necessary attributes and monitor its progress to ensure it completes successfully.
Create, update, or delete resources: After the stack is launched, CloudFormation provides the ability to create, update or delete the AWS resources defined in the stack.
Maintain the stack: Perform maintenance activities to keep the CloudFormation templates and resources up-to-date with the latest versions and security patches.
Clean up the stack: When you no longer need the CloudFormation stack, clean up the AWS resources created by deleting the stack.
One key component of a CloudFormation deployment (step 3) is the Service Role. We will explore what a CloudFormation Service Role is and the benefits it brings to managing AWS resources efficiently.
CloudFormation's Stack Creation Process
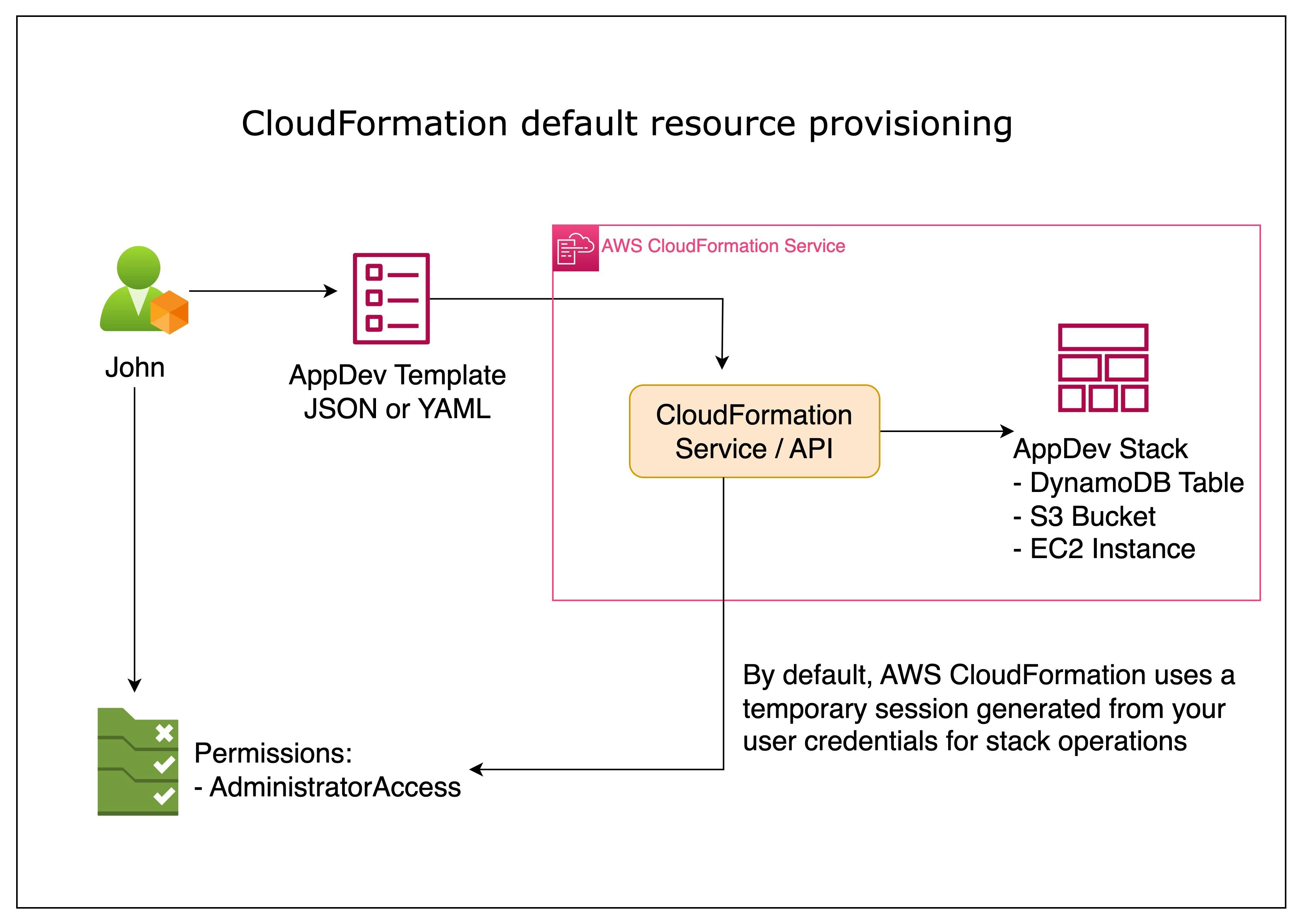
When using the AWS Management Console or the AWS CLI, by default**, AWS CloudFormation uses a temporary session generated from your user credentials** for stack operations.
This means that CloudFormation can utilize your permissions on your behalf. If you are an admin, CloudFormation will operate with admin privileges. This increases the risk of accidental alterations or malicious activities impacting other areas of your infrastructure.
Using A Service Role with CloudFormation
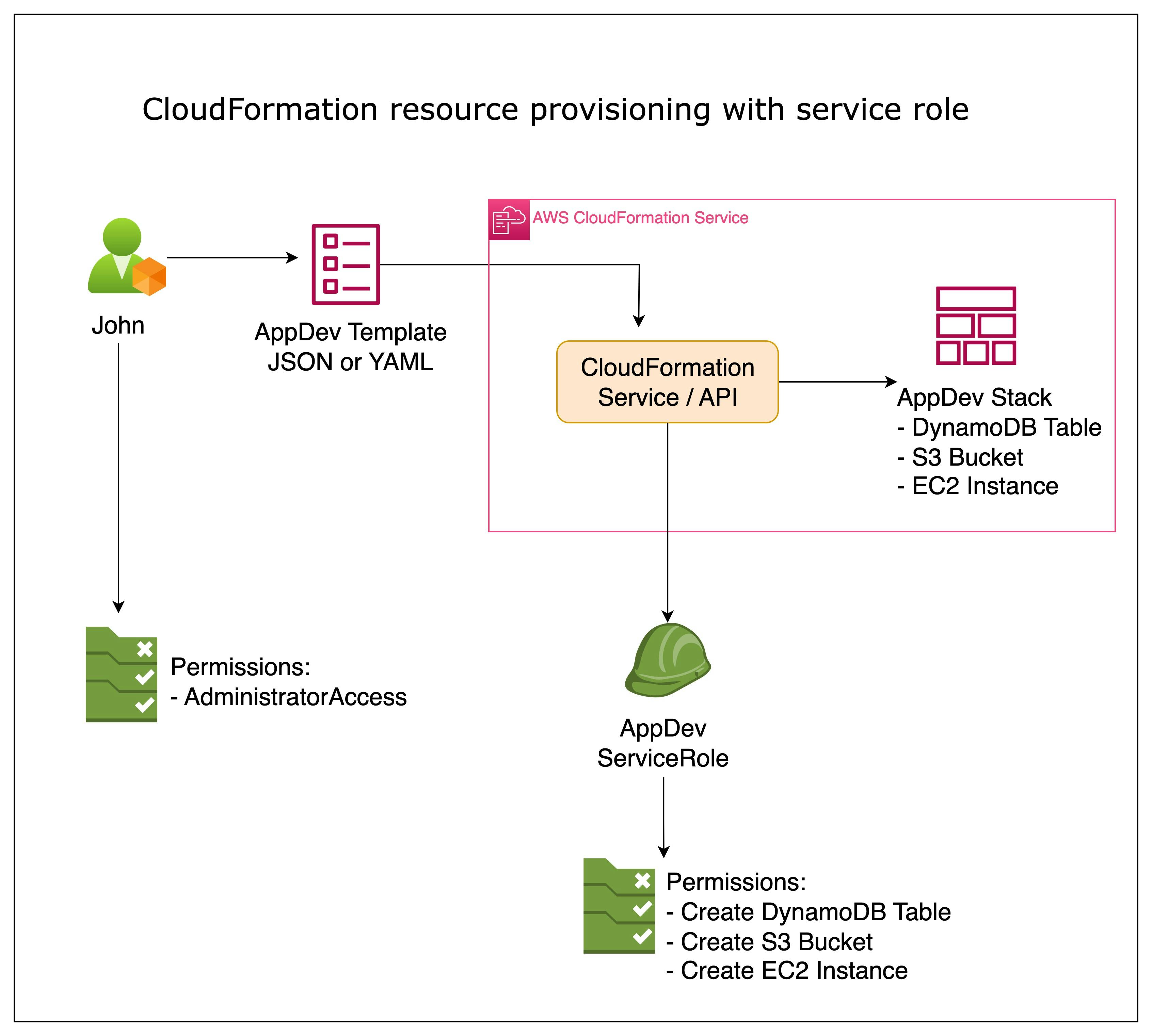
A CloudFormation Service Role is an AWS Identity and Access Management (IAM) role specifically designed to be used by CloudFormation during resource provisioning.
This role outlines the necessary permissions and policies that CloudFormation requires to create, update, or delete AWS resources specified in your templates. It serves as a trusted entity that CloudFormation assumes when performing stack operations on your behalf.
Let's walk through a quick example:
Let's create a simple CloudFormation template:
# app-dev.yaml AWSTemplateFormatVersion: 2010-09-09 Resources: AppDevBucket: Type: AWS::S3::BucketIn the YAML CloudFormation template provided, an AWS S3 resource type is defined, which creates an Amazon S3 bucket in the same AWS Region as the AWS CloudFormation stack.
Now, let's deploy the stack using CloudFormation. Instead of utilizing our local user's permissions, we will provide the ARN of the desired service role. To accomplish this, we will use the AWS CLI to deploy the CloudFormation template while specifying the service role we wish to employ.
aws cloudformation deploy \ --template-file app-dev.yaml \ --stack-name app-dev-stack \ --role-arn arn:aws:iam::__ACCOUNT_ID__:role/app-dev-cloudformation-service-roleThe IAM Role must exist prior to deploying the template. This establishes a separation layer between your application's permissions and your account's permissions. In this example, my infrastructure layer created the IAM Role called
app-dev-cloudformation-service-role, which includes the permissions-managed policy, AmazonS3FullAccess.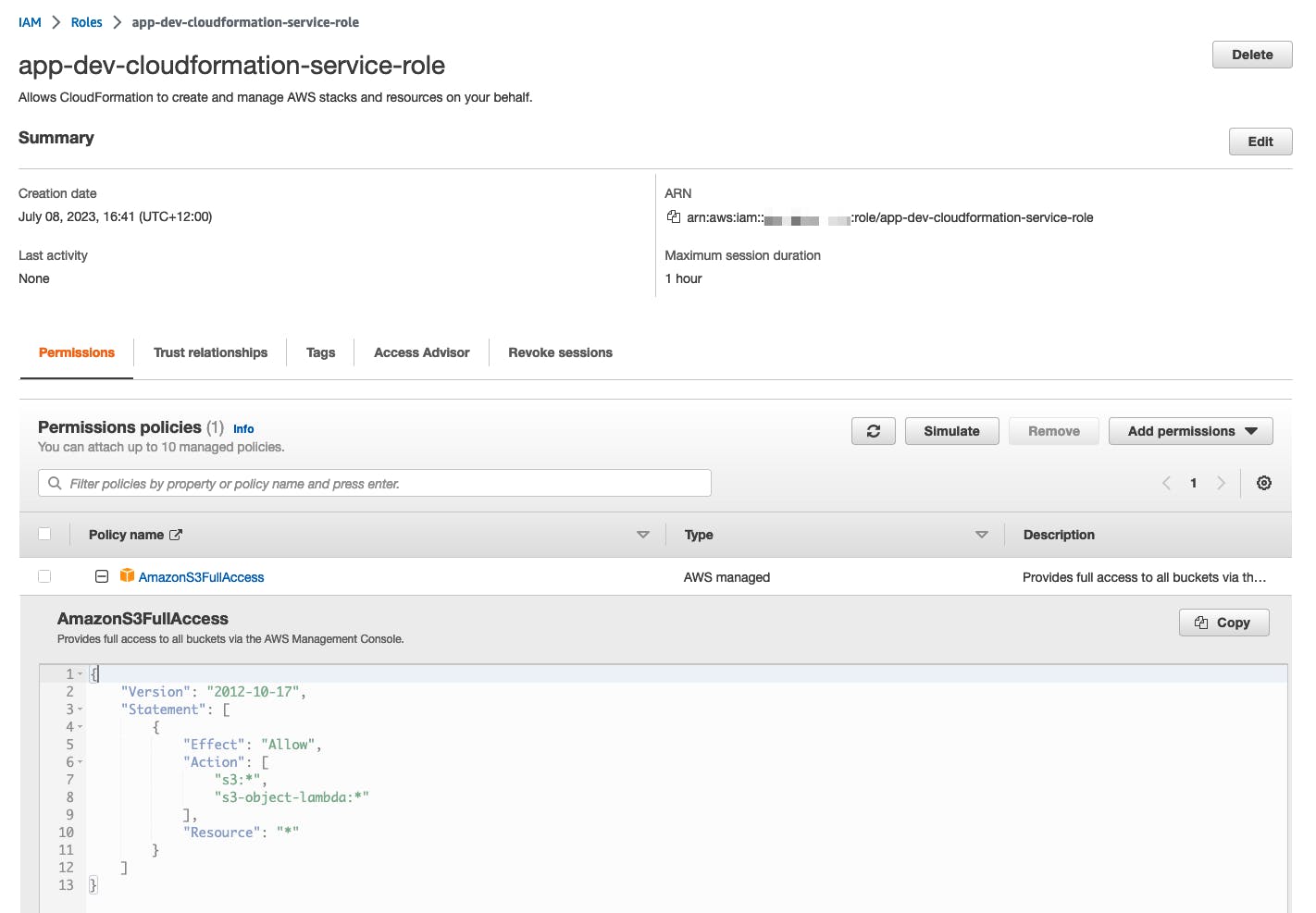
You can create the service role example using the following template:
AWSTemplateFormatVersion: '2010-09-09' Resources: AppDevServiceRole: Type: AWS::IAM::Role Properties: RoleName: app-dev-cloudformation-service-role AssumeRolePolicyDocument: Version: '2012-10-17' Statement: - Effect: Allow Principal: Service: cloudformation.amazonaws.com Action: sts:AssumeRole ManagedPolicyArns: - arn:aws:iam::aws:policy/AmazonS3FullAccessNow, you can track the deployment progress in the CloudFormation dashboard to ensure its successful completion.
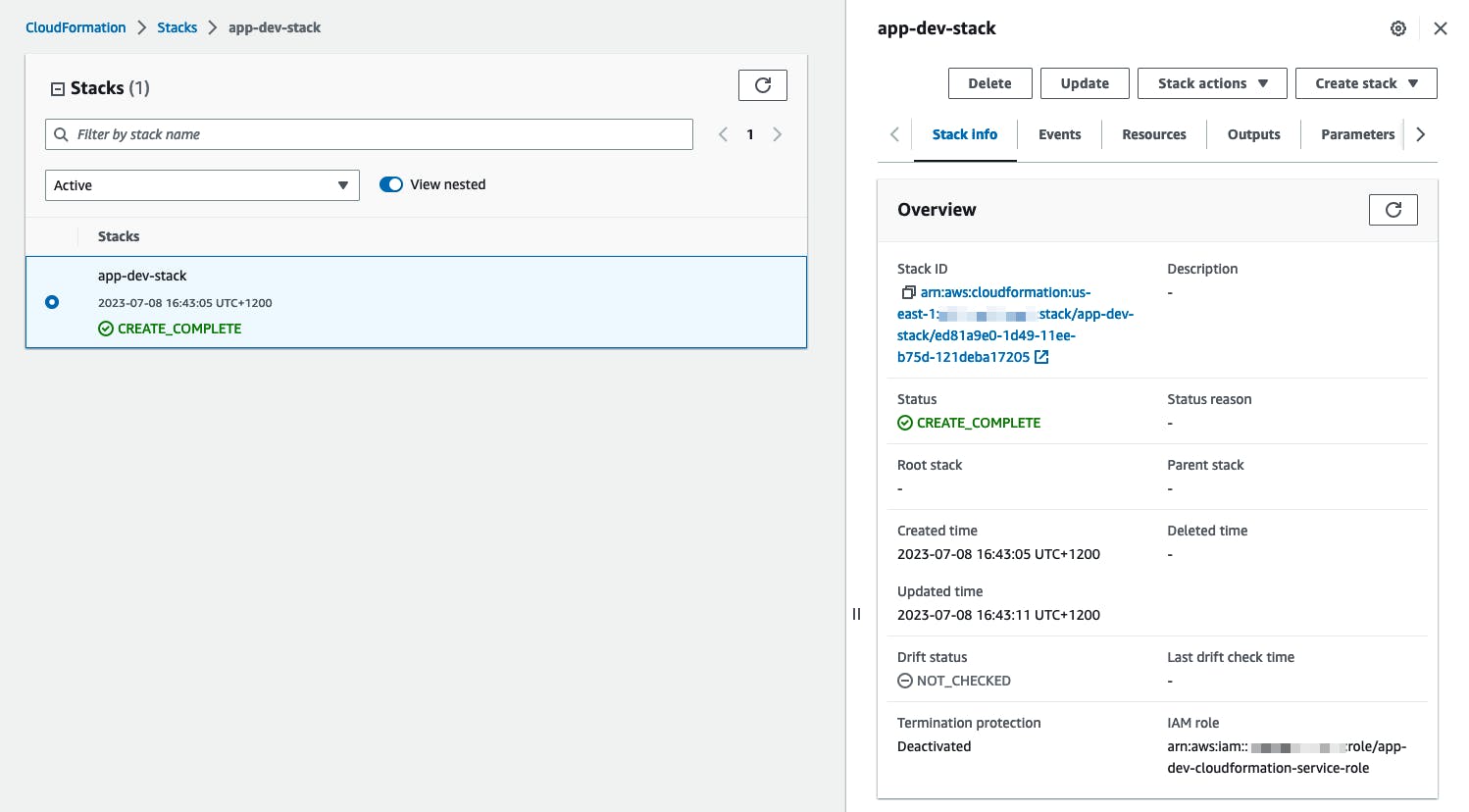
With the stack deployed, the associated IAM Role will restrict any future CloudFormation actions (create, delete, update).
Benefits of a Service Role
Utilizing a service role in conjunction with a CloudFormation stack offers numerous advantages, not only from a strict security perspective.
It allows you to follow the principle of least privilege when provisioning resources. By granting only the necessary permissions to the Service Role, you limit the potential impact of any security vulnerabilities or misconfigurations. This ensures that CloudFormation can perform its intended actions without unnecessary access to other resources or capabilities.
It eliminates the need to provide individual IAM credentials for each resource or template. As the Service Role is associated with the CloudFormation service, it automatically inherits the necessary permissions across all templates and stacks. This simplifies the provisioning process, reduces administrative overhead, and makes managing and maintaining your infrastructure as code easier.
It gives you granular control over what actions CloudFormation can perform on your behalf. You can define fine-grained policies and permissions specific to your resource provisioning requirements.
Since all CloudFormation operations are carried out under this specific role, it becomes easier to track and audit the changes made by CloudFormation in your AWS environment.
It contributes to better security and compliance practices. By leveraging IAM features like Multi-Factor Authentication (MFA) and temporary security tokens, you can add an extra layer of security to your CloudFormation operations. You can also enforce security best practices, such as defining resource-specific encryption requirements or requiring stricter access controls through IAM policies.
It strictly separates concerns between CloudFormation and other AWS services or resources. Since the Service Role is isolated to CloudFormation, it reduces the risk of accidental changes or malicious actions affecting other parts of your infrastructure. It also promotes a modular approach to infrastructure provisioning, making it easier to manage and troubleshoot your templates and stacks individually.
Conclusion
The CloudFormation Service Role simplifies and enhances the experience of deploying and managing AWS resources using infrastructure-as-code principles. By assigning the appropriate permissions to the Service Role, you can ensure secure and efficient resource provisioning while adhering to the principle of least privilege.
Through granular control, enhanced security, and improved auditability, the Service Role brings added benefits to your CloudFormation workflows.
By leveraging the power of a dedicated Service Role, you can ensure effective cloud infrastructure management and focus on delivering value to your organization.
Frequently Asked Questions
What is AWS CloudFormation?
AWS CloudFormation is a service that allows developers to define and manage infrastructure using code, simplifying the process of provisioning and managing AWS resources.What is a CloudFormation Service Role?
A CloudFormation Service Role is an AWS Identity and Access Management (IAM) role specifically designed for CloudFormation to assume when performing stack operations, such as creating, updating, or deleting AWS resources specified in your templates.How does a Service Role improve security in CloudFormation?
A Service Role follows the principle of least privilege, granting only the necessary permissions for CloudFormation to perform its tasks, reducing the risk of accidental changes or malicious actions affecting other parts of your infrastructure.What are the benefits of using a Service Role in CloudFormation?
Benefits include granular control over actions, enhanced security, improved auditability, reduced administrative overhead, and a modular approach to infrastructure provisioning.How can I create and use a CloudFormation Service Role?
First, create an IAM role with the necessary permissions for your resource provisioning requirements. Then, when deploying your CloudFormation stack, specify the ARN of the desired service role using the AWS CLI or the AWS Management Console.
Are you interested in more?
Head over to our bi-weekly newsletter or check out the following blog posts

