Are you curious about one of the most powerful and my favorite services Amazon Web Services offers?
Look no further than AWS Config!
In this article, we'll dive into the ins and outs of this service that provides a detailed view of the configuration of your AWS resources.
AWS Config is a must-have for keeping track of your resources and monitoring changes over time. So let's get started and explore the world of AWS Config!
Infographic
Let's start with a one-minute overview in this one-pager:
AWS Config Overview
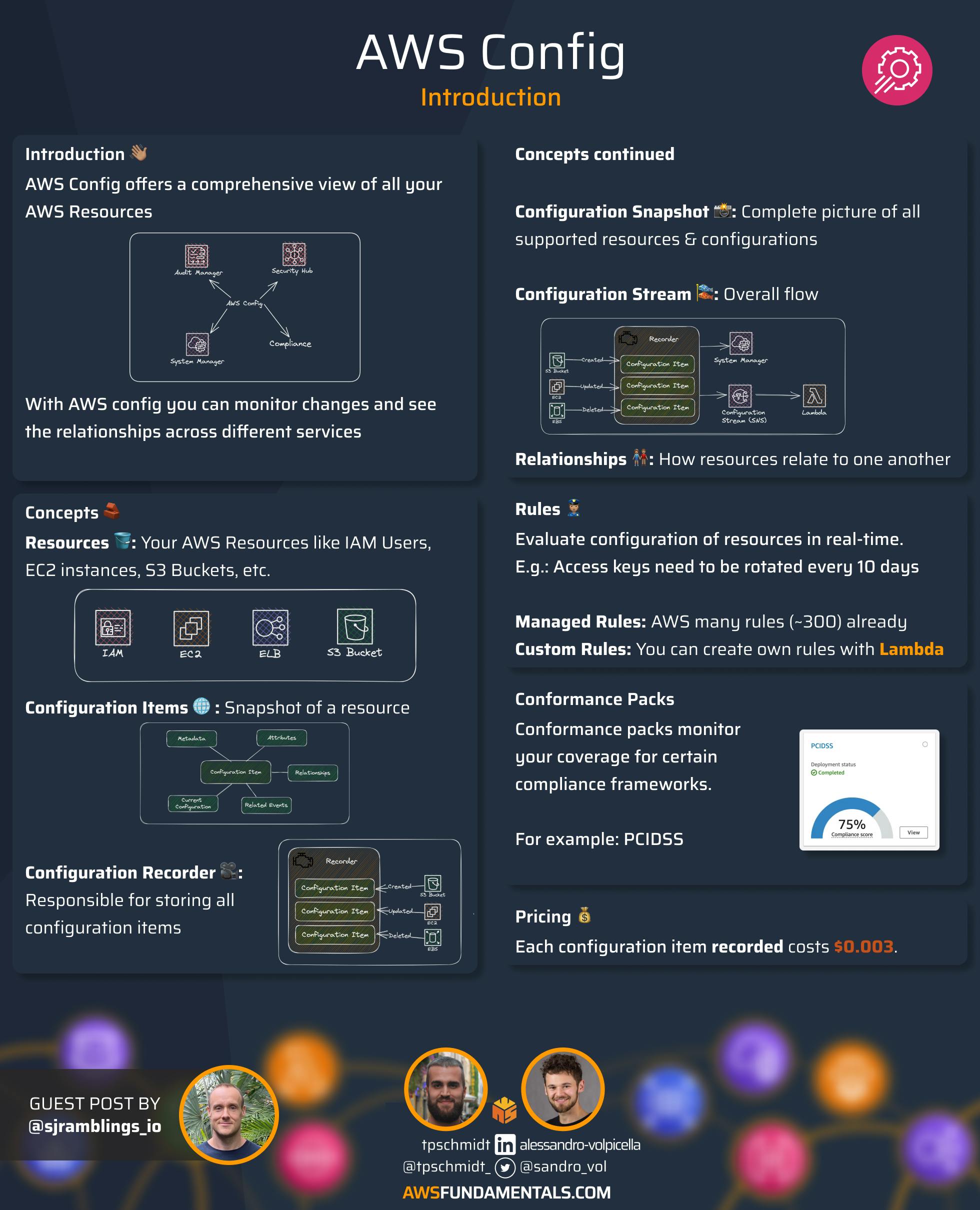
AWS Config provides a comprehensive view of the configuration of your AWS resources. It keeps track of all the configuration attributes of supported resources within your AWS Account, including how resources are related to one another and how they were configured in the past.
Once AWS Config is enabled, you can easily monitor changes to your resources over time, identify potential security risks, react to those risks, and ensure compliance with industry standards and best practices.
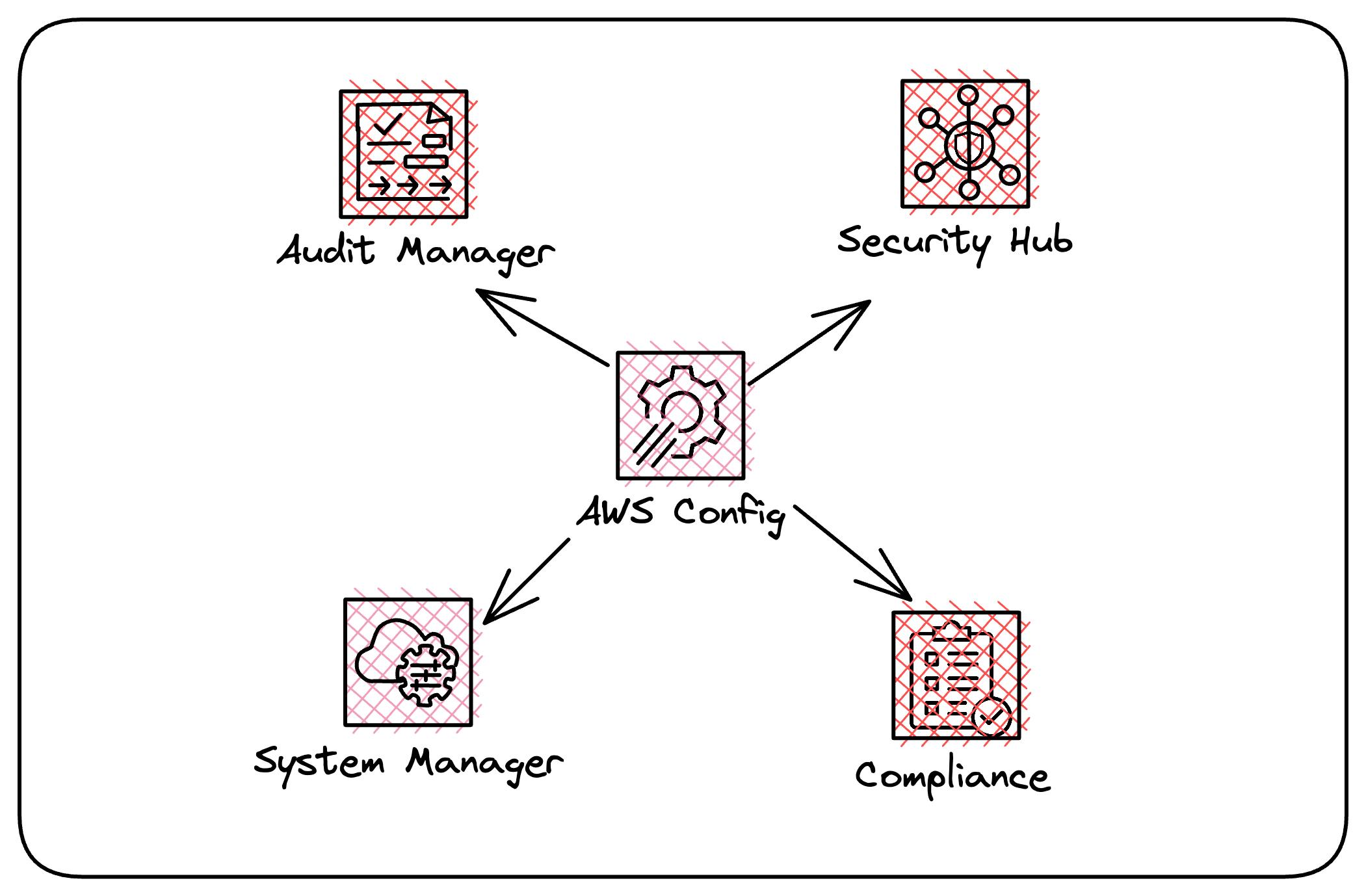
AWS Config is an essential tool for managing your AWS resources and maintaining a secure and compliant environment. It's also used to feed other AWS Services such as Security Hub, Audit Manager, and Systems Manager.
AWS Config Concepts
First, let's go through some of the foundational concepts of the service to help you understand how it all hangs together.
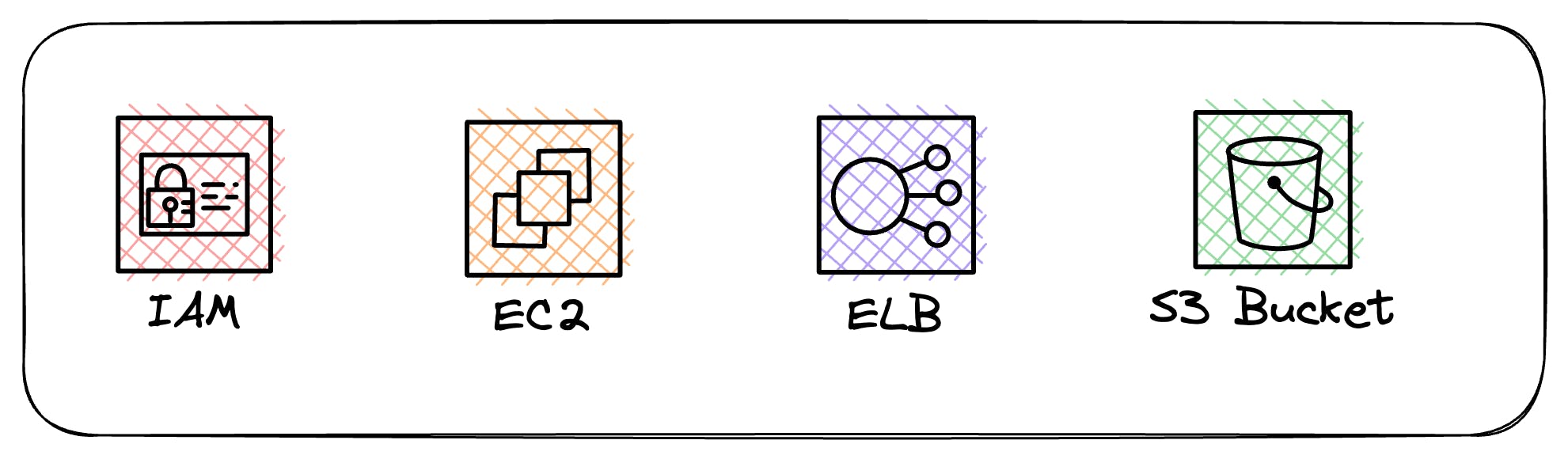
Resources
We create resources through the Console, Cli, or your favorite IAC tools such as Cloudformation or Terraform. These resources include IAM Users, EC2 Instances, EBS Volumes, S3 Buckets, and more.
As long as the resource is on the supported resources list for AWS Config, it will keep track of it for you.
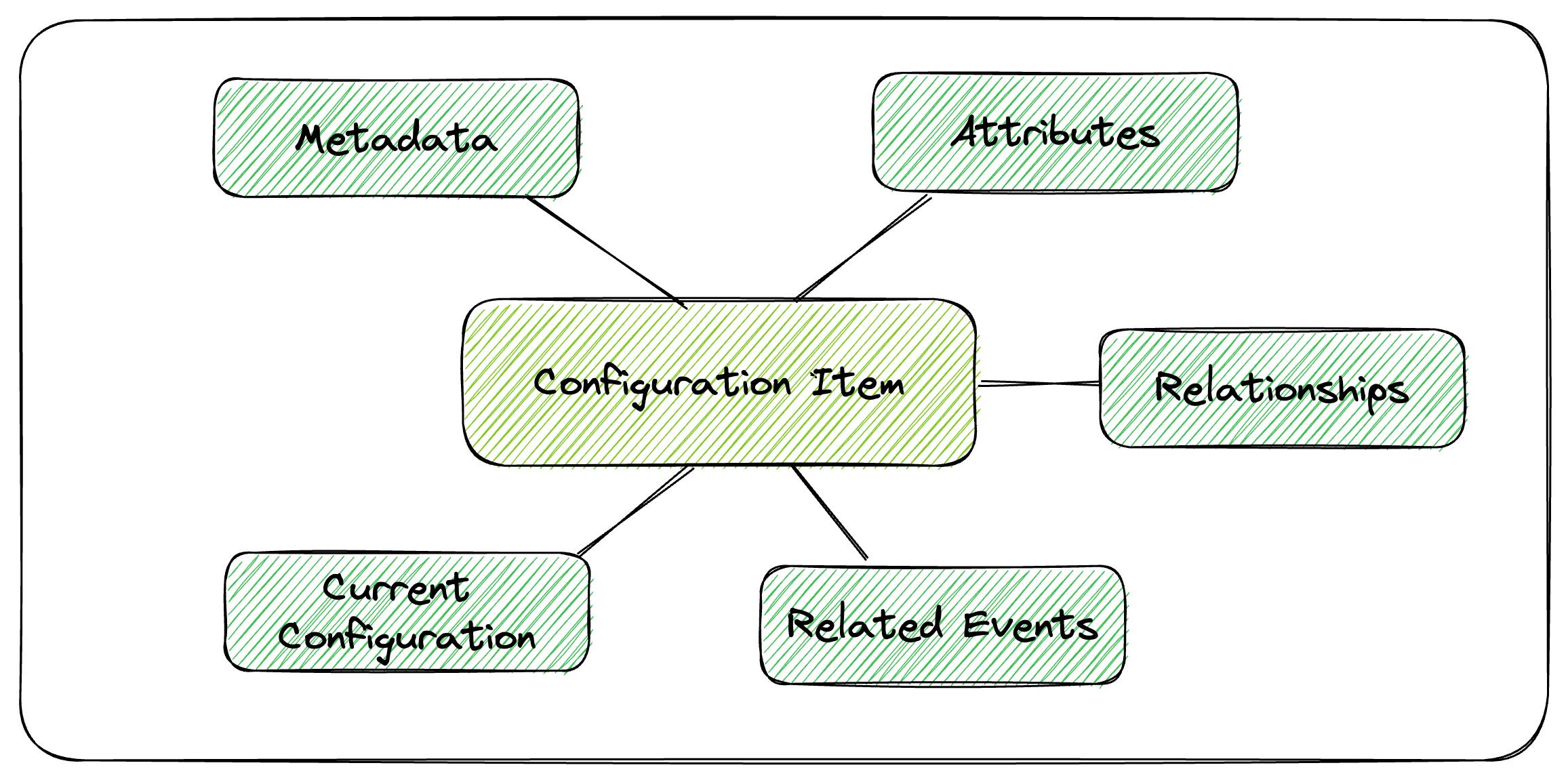
Configuration Items
A configuration item is a snapshot of a supported resource at a specific point in time. It includes metadata, attributes, relationships, current configuration, and related events.
These configuration items are the building blocks that AWS Config uses to provide the configuration history of your AWS Resources.
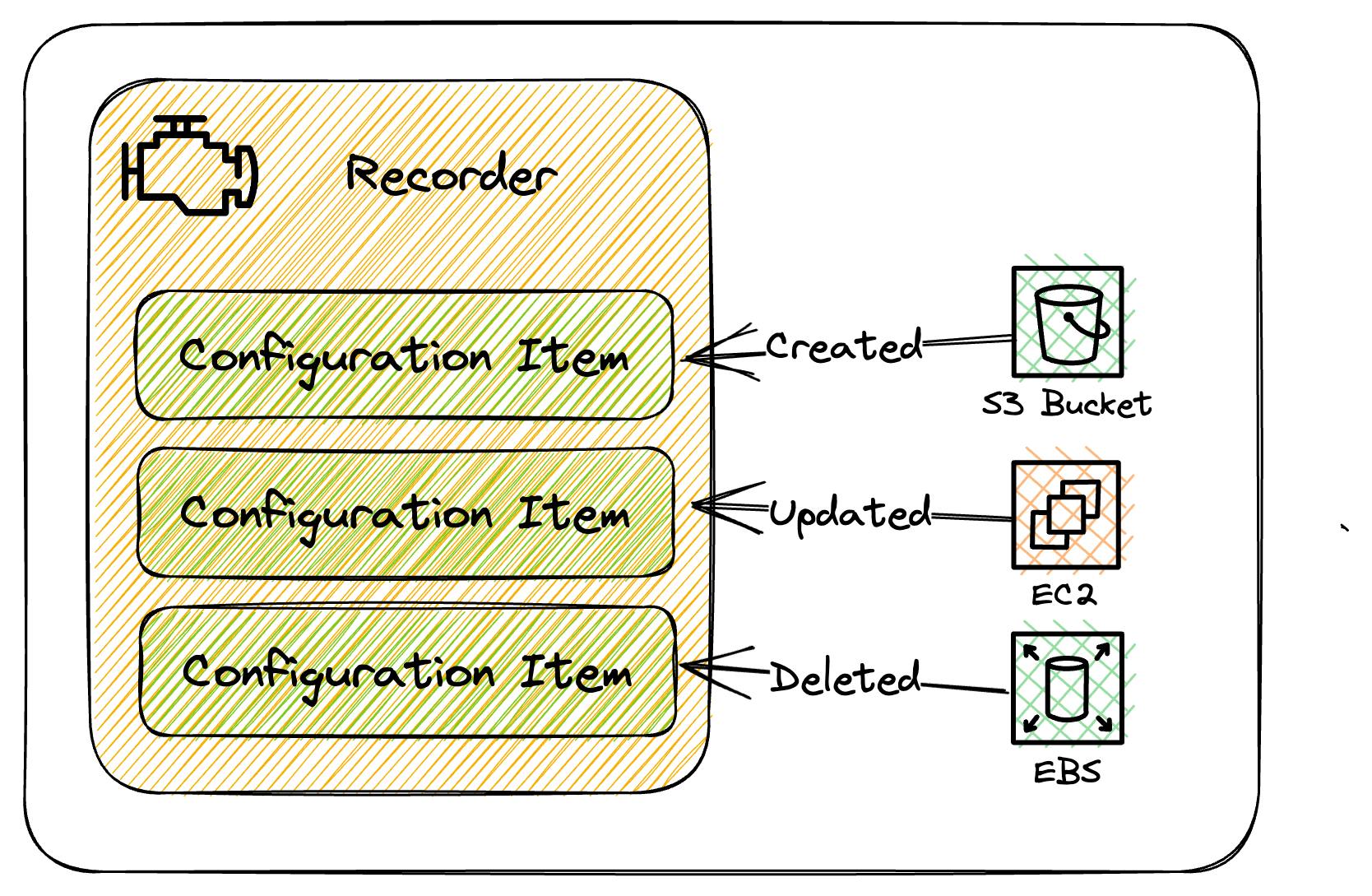
For example, if AWS Config is recording Amazon S3 buckets, AWS Config creates a configuration item whenever a bucket is created, updated, or deleted
Configuration Recorder
Think of Configuration Recorder as the engine that's responsible for storing all the configuration items for all supported resources within the region where AWS Config is running.
By default, the Configuration Recorder will store configuration items for all supported resources, but you can select a subset of resources if needed.
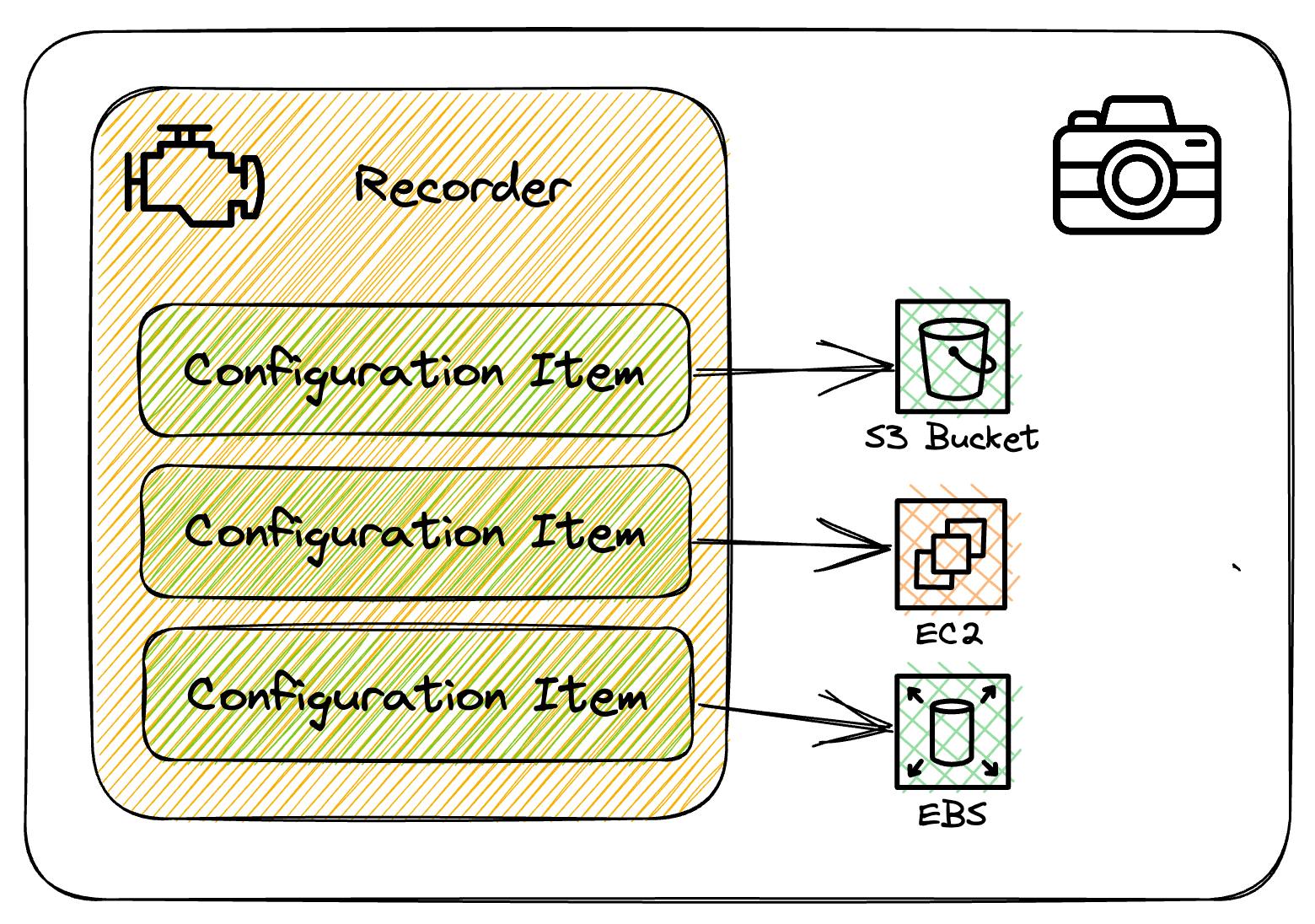
Configuration Snapshot
A configuration snapshot is a complete picture of the supported resources that exist in your account and their configurations. It's a collection of the configuration items that have been recorded, and it can be a useful tool for validating your configuration.
This snapshot provides a comprehensive view of your AWS resources, making it easier to ensure that everything is configured correctly.
These can be delivered to S3 or viewed in the AWS Config console.
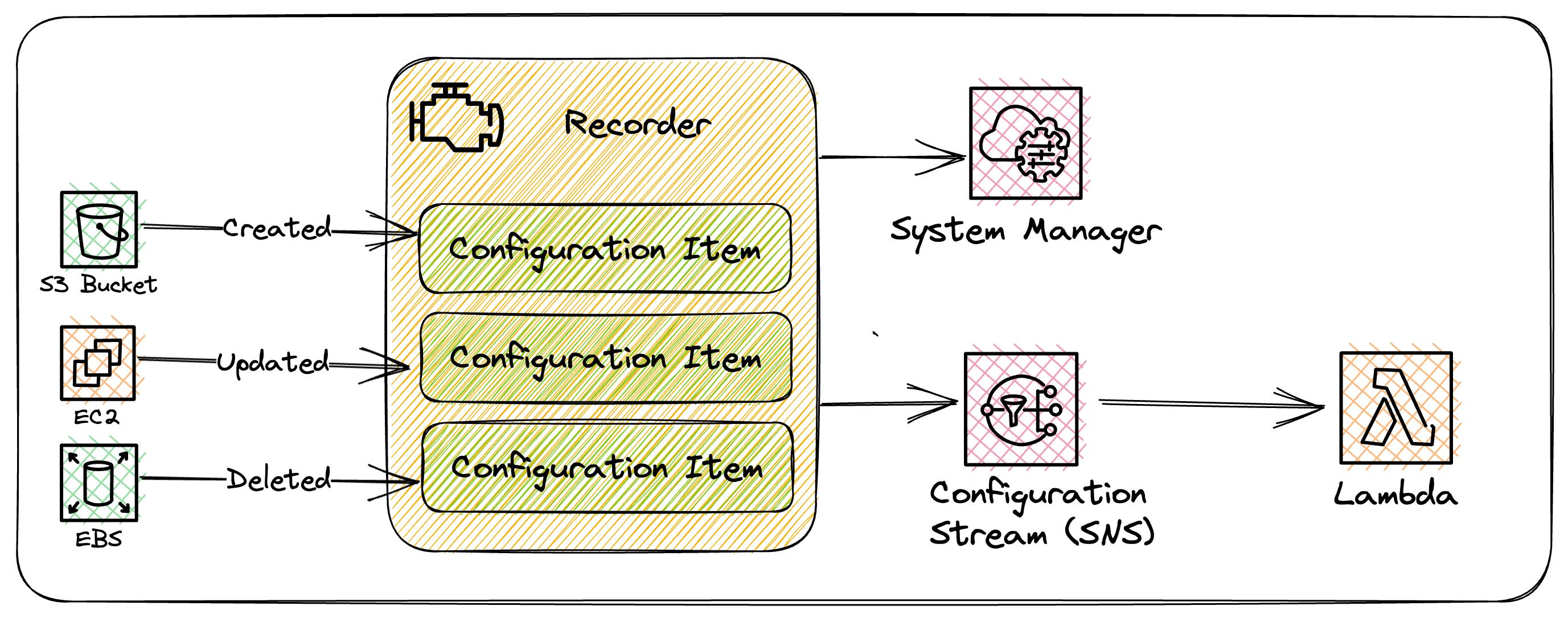
Configuration Stream
The configuration stream is the firehose of all the updates to those supported resources. Whenever a resource is created, modified, or deleted, AWS Config creates a configuration item and adds them to the configuration stream.
This stream is very powerful in that we can react to these events directly using Systems Manager or using other AWS services such as Lambda and many others.
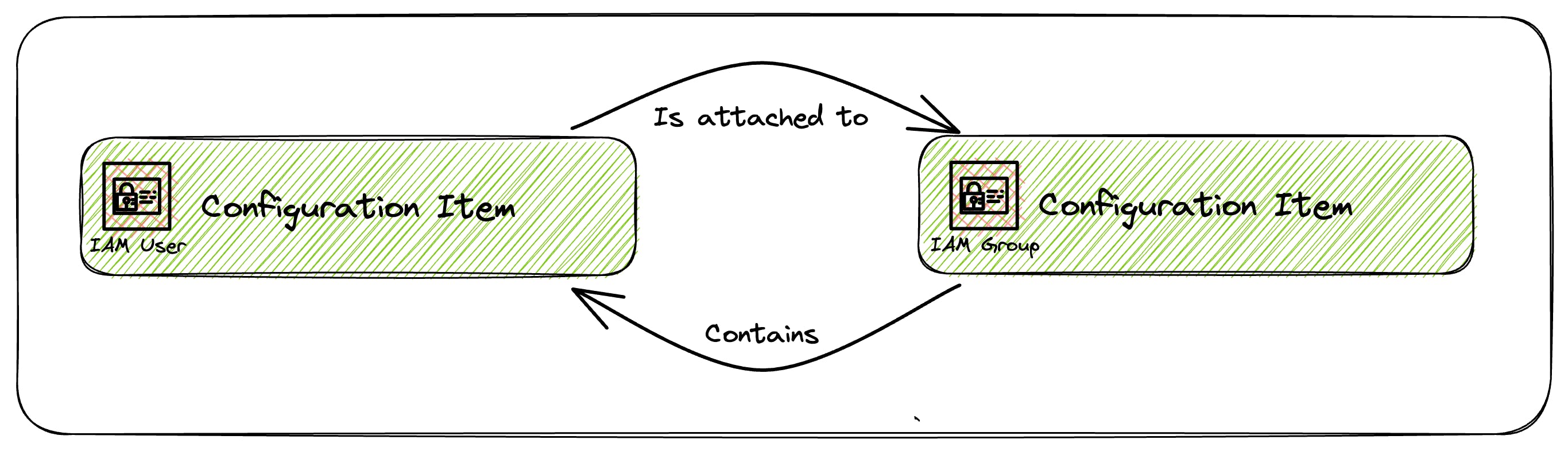
Relationships
Relationships provide information on how configuration items relate to one another, giving us a better picture of our resources.
For example:-
An IAM User configuration item could have a relationship with an IAM Group if it was a member of the Group.
An EC2 instance might include a relationship with an EBS Volume.
These relationships help to provide more context of how our resources are related.
Remediation
Remediation allows us to fix stuff through automation if AWS Config detects a rule is NON_COMPLIANT. This is all driven through AWS Systems Manager Automation documents.
For example, we can deploy the 'restricted-ssh' rule to ensure none of our EC2 instances has open ssh access. If AWS Config detects a NON_COMPLIANCE for this rule it can trigger an SSM Automation Document to remove it.
This is all triggered in near real-time via the Configuration Stream described above.
AWS Config Rules
Rules give us a way to evaluate the configuration of our resources in near real-time.
They tap into the configuration stream as resources are created or updated and compare the configuration to a desired state defined in the rule. If the configuration of the resource deviates from the rule then it is marked as NON_COMPLIANT.
There are two types of rules Managed & Custom.
Managed Rules
Managed rules are provided by AWS. We can pick which ones are relevant to our environment and deploy them through the AWS Console, Cli or IAC tools. A full list is available here.
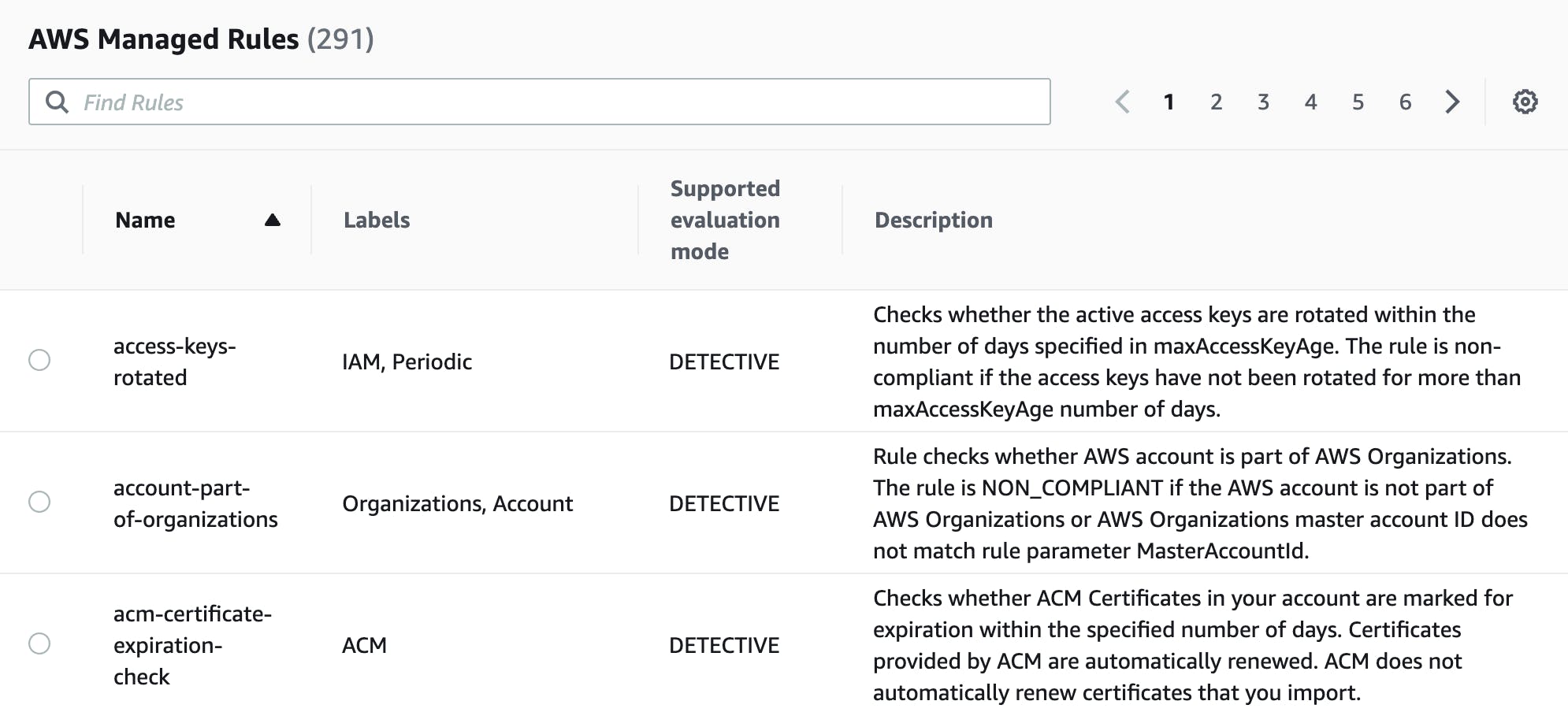
Managed rules are also used by other AWS Services such as Security Hub to report overall compliance of resources within the AWS Account.
Custom Rules
We can also create our own rules either using the AWS Console, cfn-guard, or the AWS Config Rules Development Kit.
Custom rules are backed by Lambda and are a bit of an advanced topic that we won't be covering here.
Conformance Packs
Conformance packs are simply a collection of rules and remediations that you can deploy and monitor as a single collection in your AWS Account. They cover all sorts of security compliance frameworks such as PCI DSS but also operational best practices for things like monitoring, autoscaling, etc.
Setting Up AWS Config
To set up AWS Config within the console
Sign in to the AWS Management Console and open the AWS Config console at https://console.aws.amazon.com/config/.
If this is the first time you are opening the AWS Config console or you are setting up AWS Config in a new region, the AWS Config console page looks like the following:

Choose 1-click setup to launch AWS Config based on AWS best practices. You can also choose Get started to go through a more detailed setup process.
Once the AWS Config service is set up we can start deploying Rules & Conformance Packs.
Deploying Rules
Rules can be deployed through the AWS Console, Cli or IAC tools. Here are the steps to deploy through the AWS Console.
Choose Add rule
Next, select one of the AWS-managed rules. There are currently over 291 to choose from!
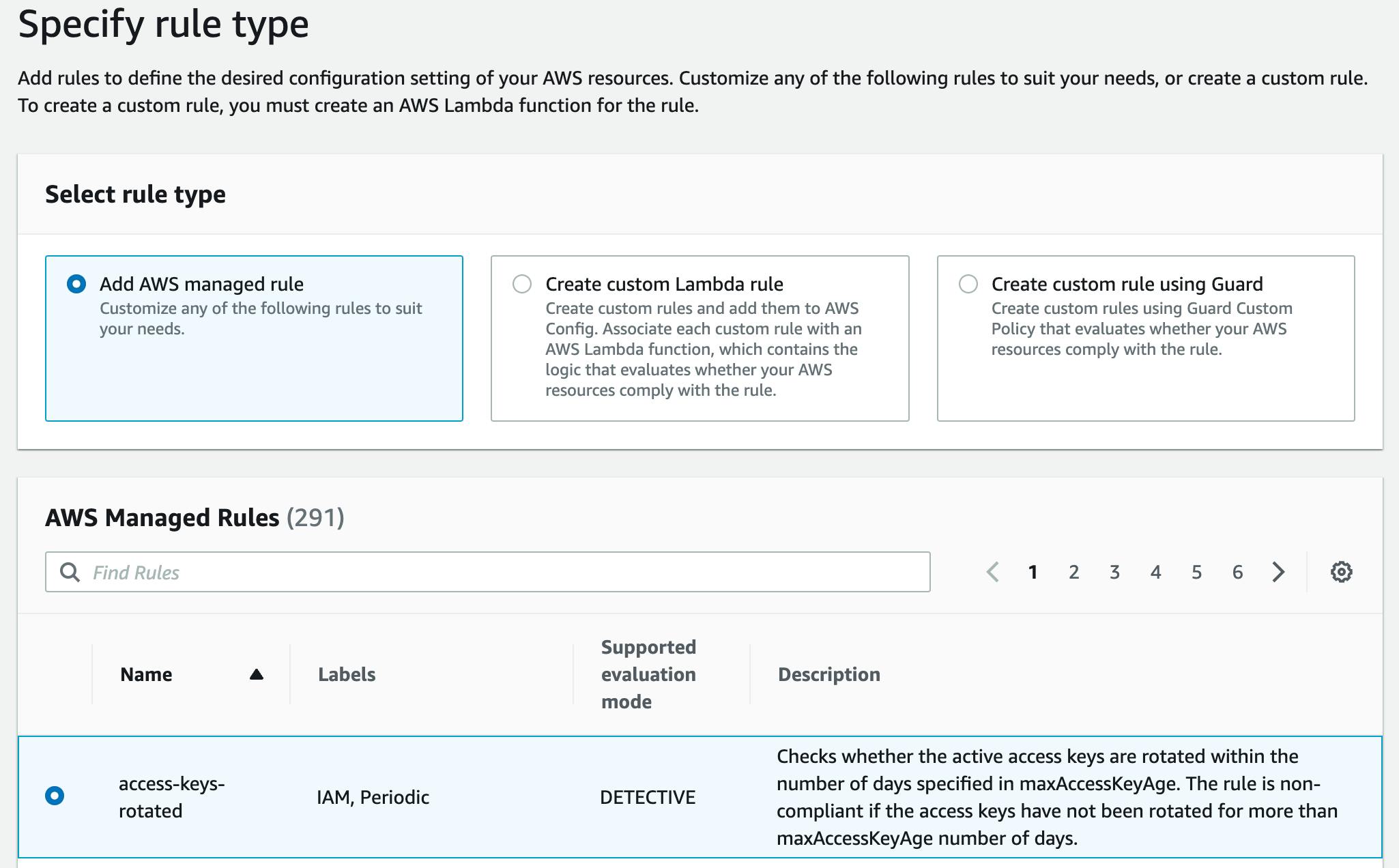
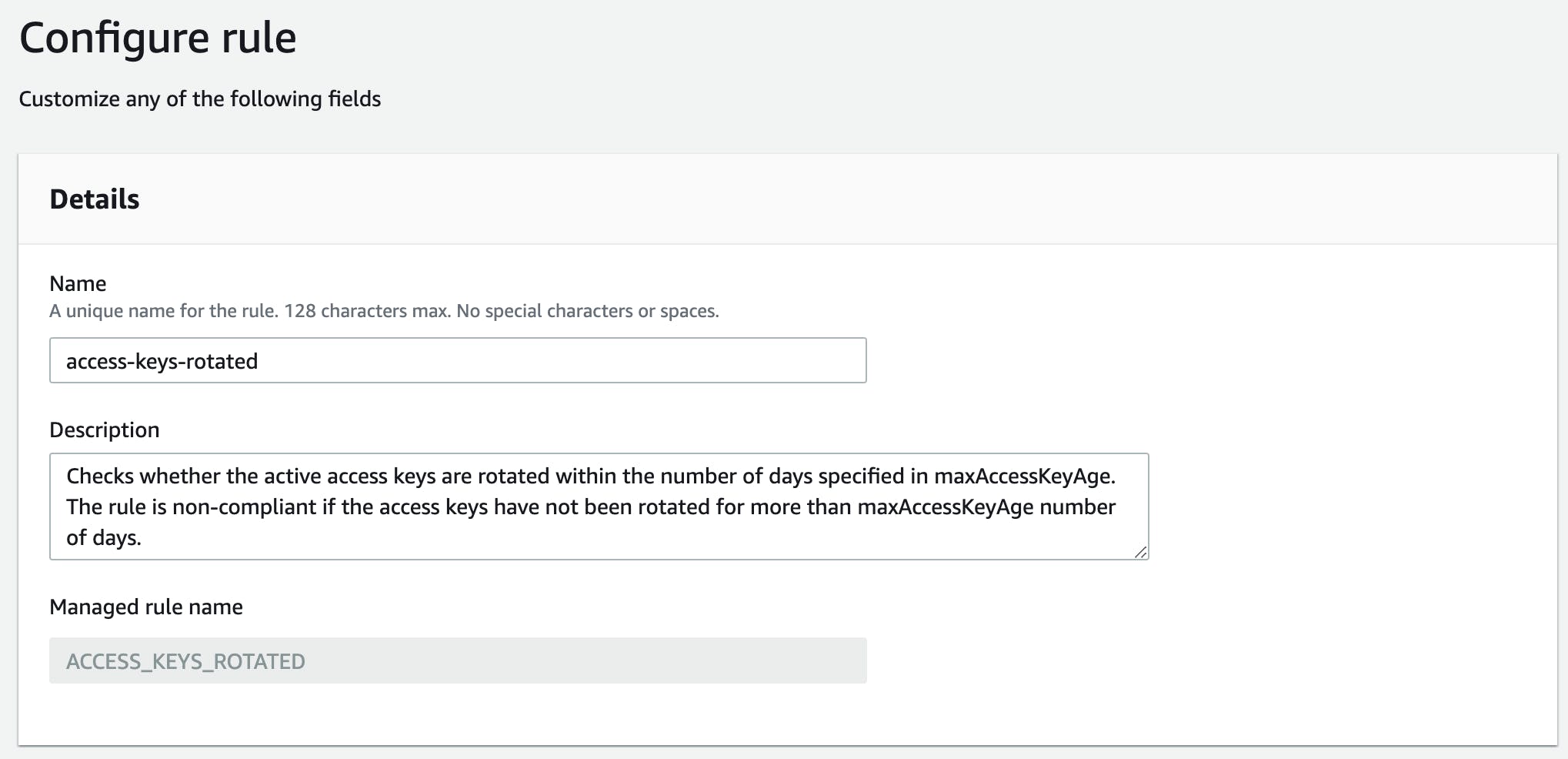
Next, give it a meaningful name.
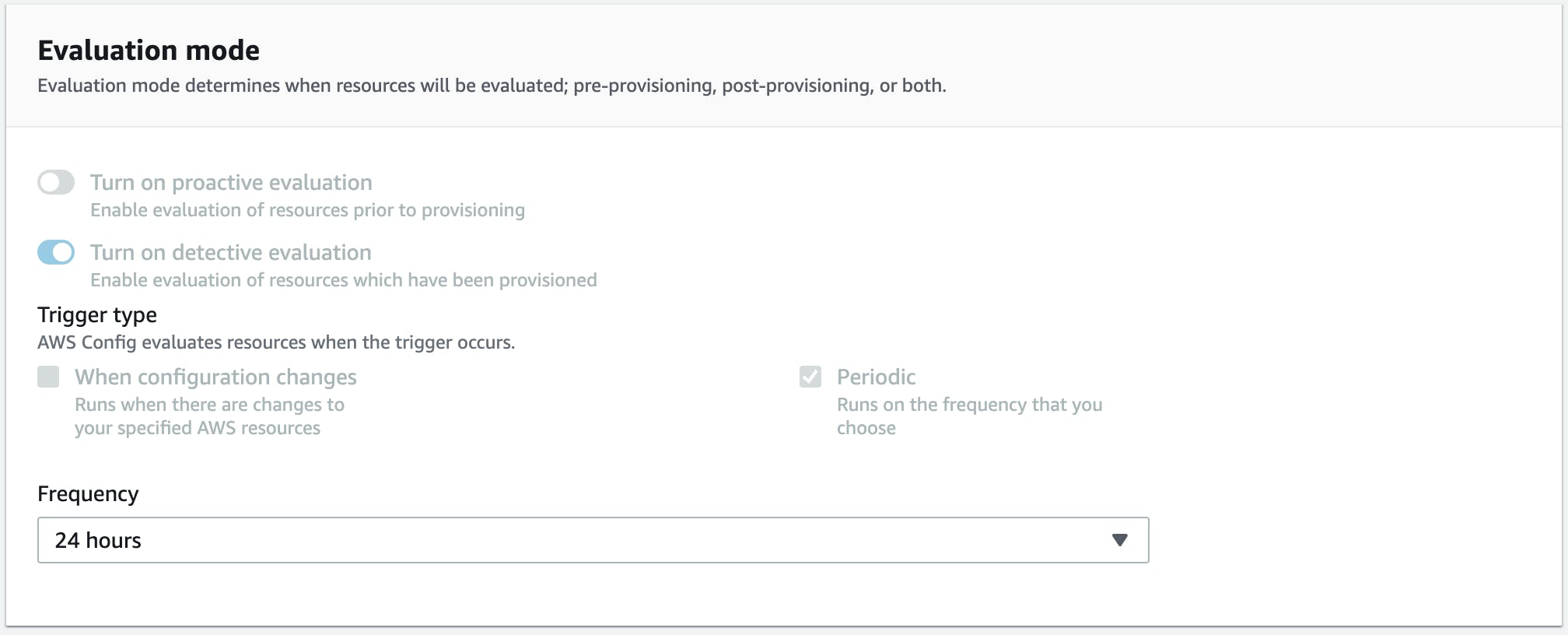
Select the type of evaluation. We can run these rules based on configuration changes to our resources or periodically.
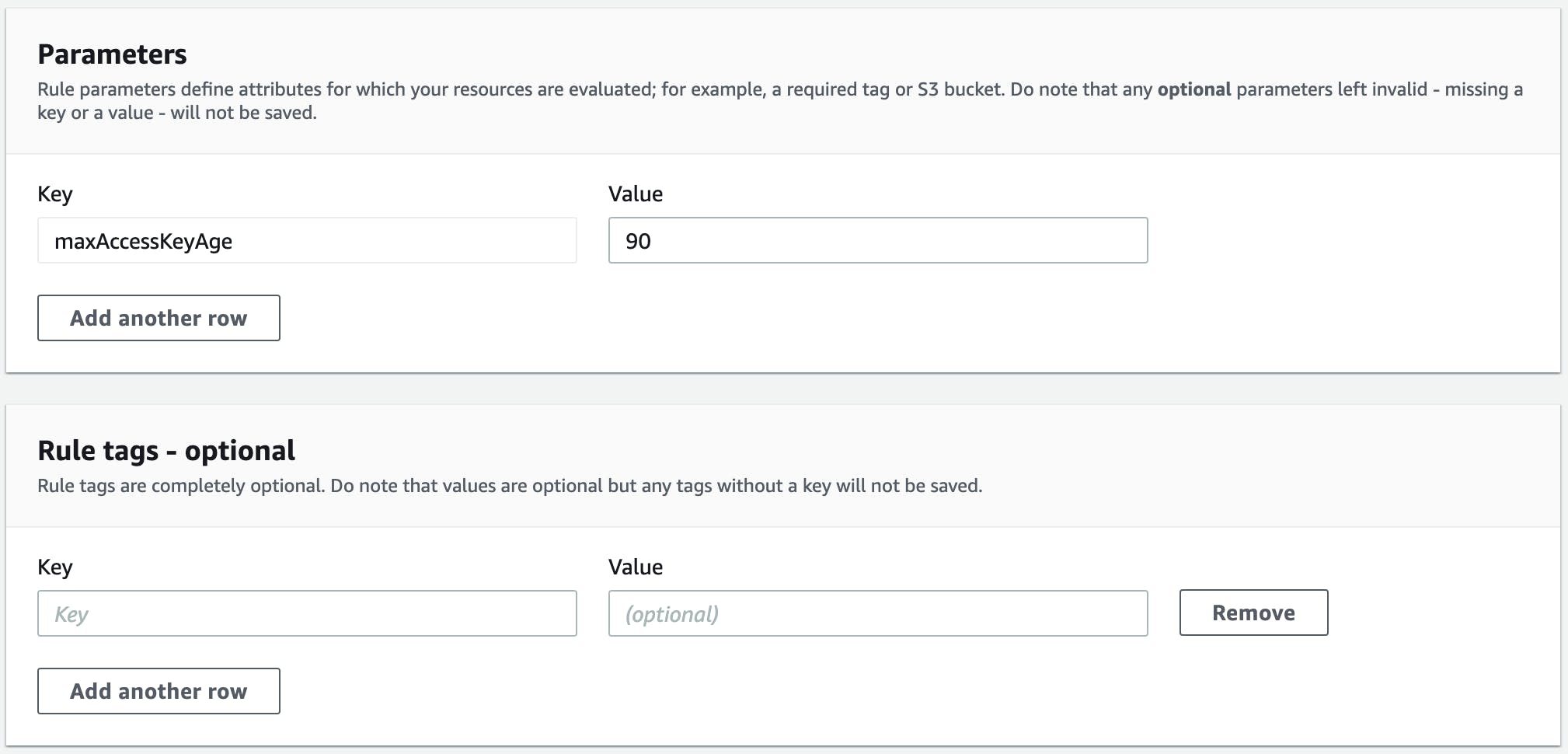
Rules can also have parameters that control how the rule will function. Here we are setting the maximum access key age to 90 days.
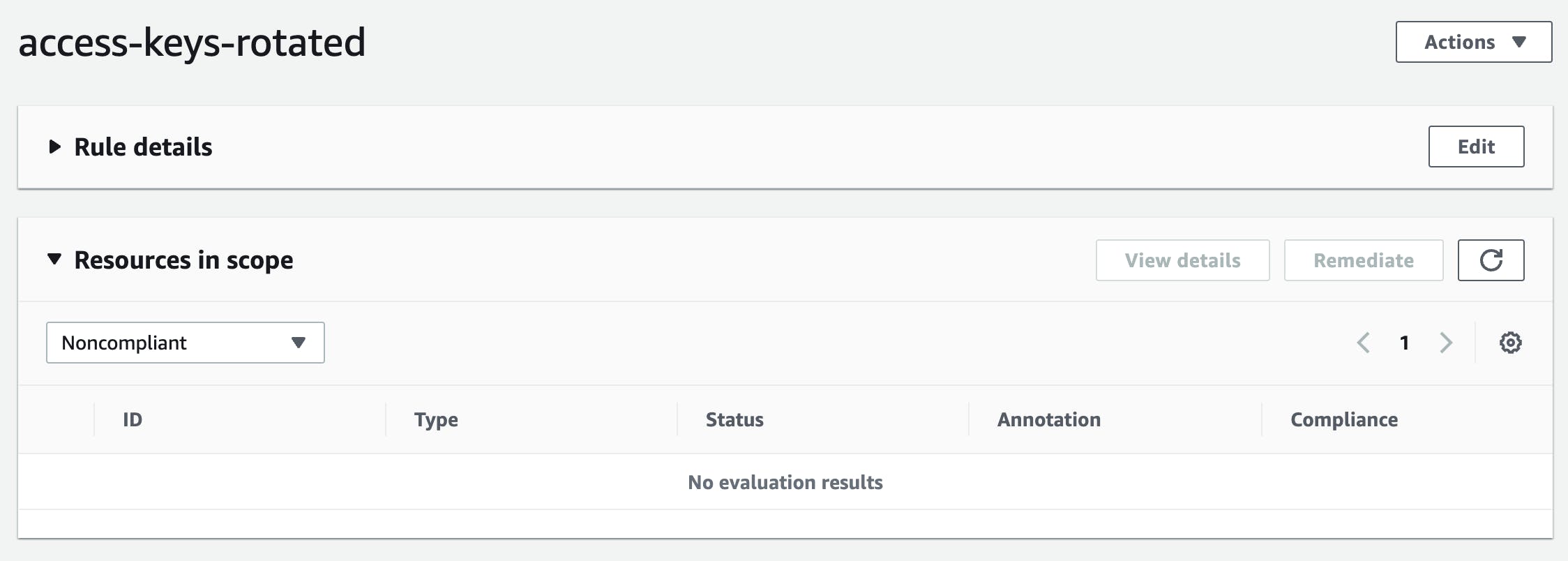
Once our rule is deployed it can be reviewed in the Console and will show any compliant or non-compliant resources associated with it.
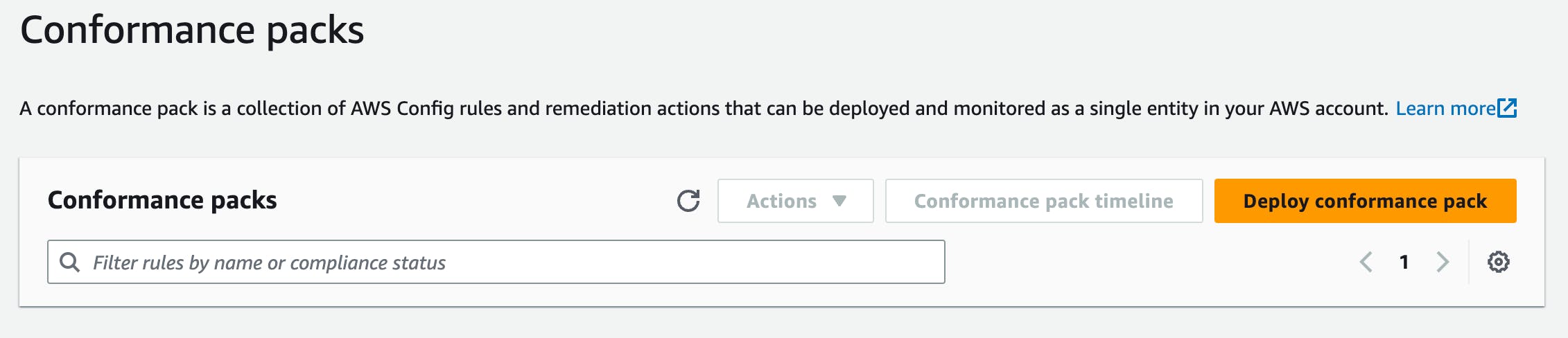
Deploying Conformance Packs
You can deploy them through the AWS Console by choosing Deploy conformance pack.
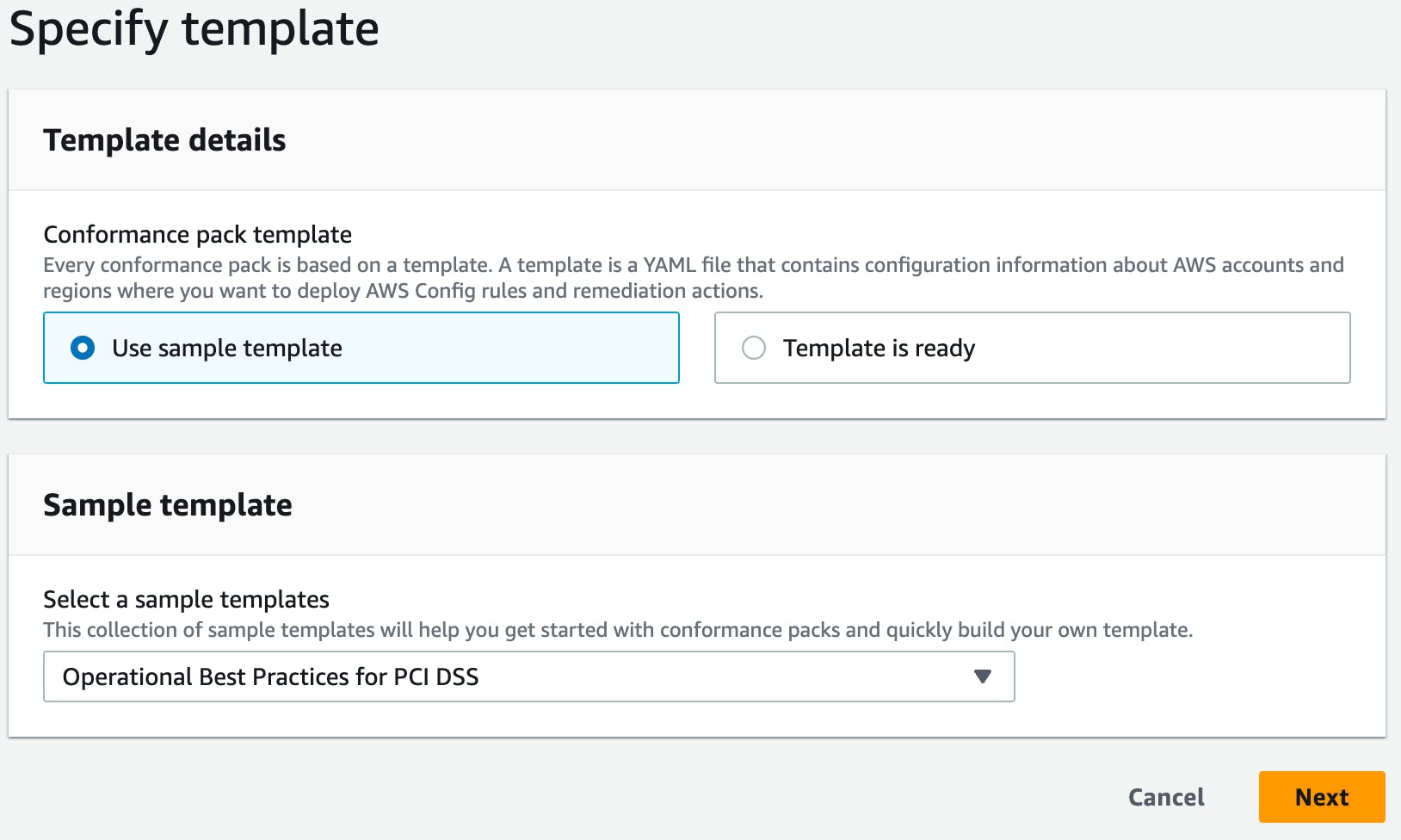
Select one of the sample templates
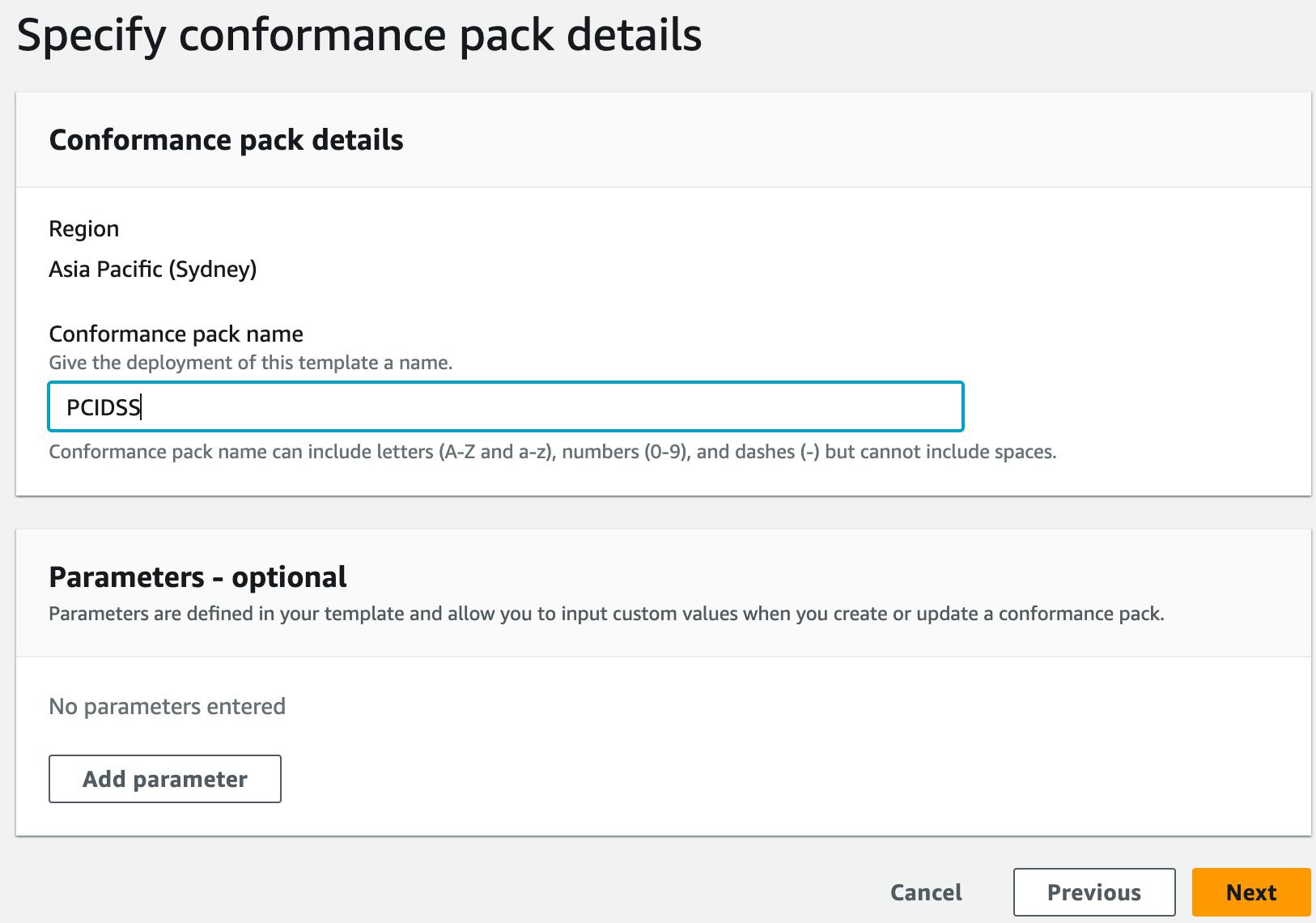
Give it a name
Choose Deploy conformance pack
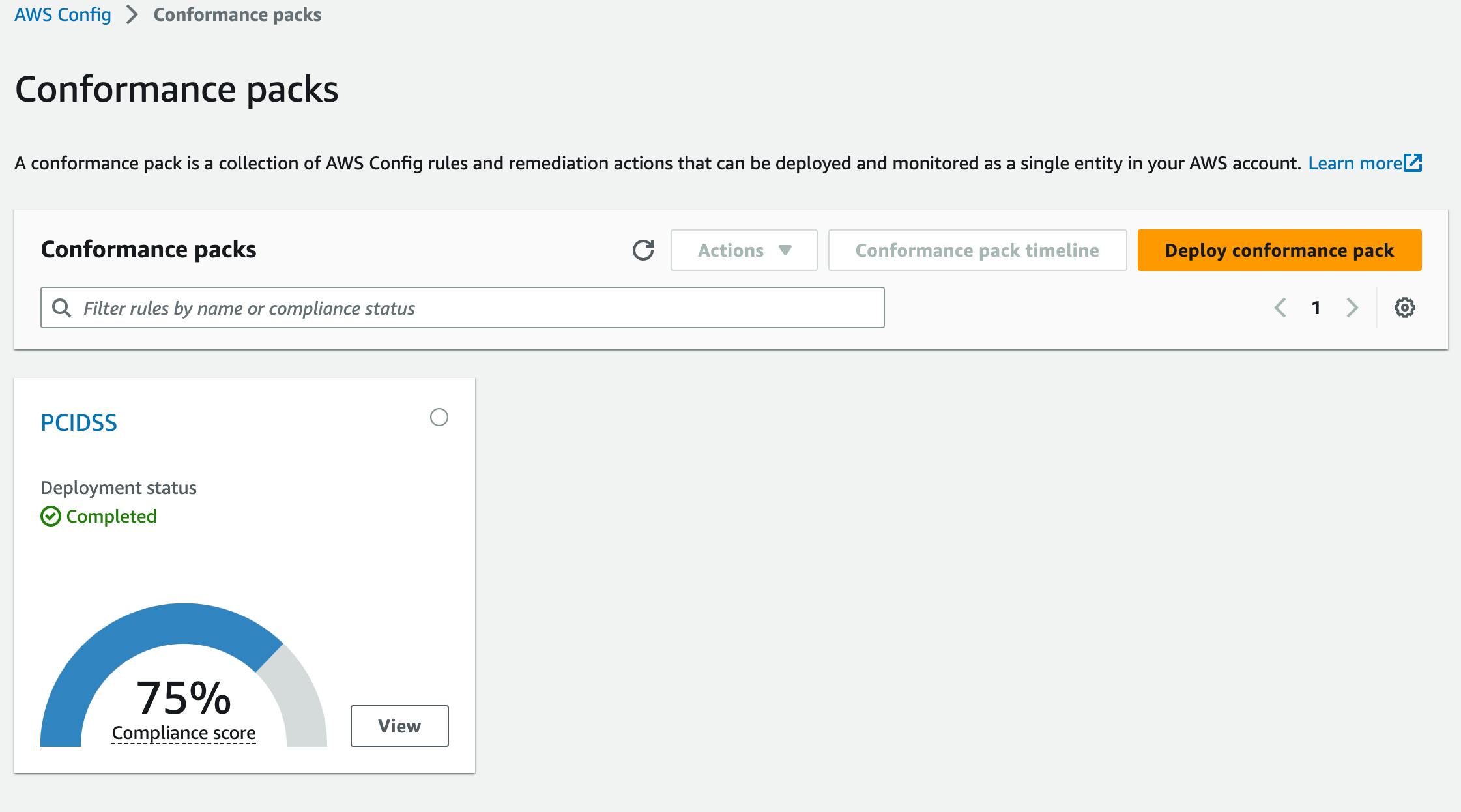
Once complete you will get a summary of the compliance score for all rules within the conformance pack.
Pricing
As with all things AWS, they come at a cost. AWS Config has had a bad reputation for being expensive, but it is more reasonable since a previous pricing update.
There are a few aspects to the pricing model.
Configuration Items
You pay $0.003 per configuration item recorded in your AWS account per AWS Region.
That means whenever a supported resource is created, updated or deleted you'll be charged.
Config Rules
Rules are charged on the number of times they are evaluated. That means whenever a supported resource is created, updated or deleted the rule will be evaluated.
| AWS Config rules evaluations | Price |
| First 100,000 rule evaluations | $0.001 per rule evaluation per region |
| Next 400,000 rule evaluations (100,001-500,000) | $0.0008 per rule evaluation per region |
| 500,001 and more rule evaluations | $0.0005 per rule evaluation per region |
Summary
In this post, we introduced you to the AWS Config concepts and walked through a few of the AWS Console screens to deploy Rules & Conformance Packs.
I hope you enjoyed the information here and are ready to go and learn more about the superpowers of AWS Config.
Thanks!